Guide to HIPAA-Compliant Digital Marketing

This guide defines how to compliantly own your organization's digital marketing strategies to create quality patient engagement that proves ROI and better patient outcomes.
Digital marketing is a cost-effective and efficient way for healthcare marketers to increase consumer engagement, improve experience, and drive better health outcomes. However, you must ensure this digital engagement happens safely and securely with a HIPAA-eligible and HITRUST-compliant tool.
HIPAA
First, let’s start by defining The Health Insurance Portability and Accountability Act of 1996 (HIPAA). HIPAA is a federal law that created national standards to protect sensitive patient health information (PHI) from being disclosed without the patient’s consent or knowledge. The HIPAA Privacy Rule implements the requirements of HIPAA.
The Privacy Rule standards address the use and disclosure of individuals’ PHI by entities subject to the Privacy Rule. These individuals and organizations are called “covered entities.” As a healthcare provider organization, you fall in the category of entities subject to following these rules to protect PHI and your technology providers.
Confusingly, there is no federal certification that constitutes “HIPAA Certification.” Many regulations control your use of PHI and personal identifiable information (PII) – the combination of those controls allows you to adhere to HIPAA privacy rules safely.
PHI
PHI is personal health information that you can think of as the PII that ties your unique ID to your health information. Safely managing your patients’ and members’ PHI allows you to use data to target and personalize their journeys to engage in the most effective communications. The existing data you have on your patients, which is PHI, is your most valuable asset. This data gives you direct access to their needs and a unique ability to target the right patient with the proper care.
Ultimately, to use PHI confidently, your organization must take all available precautions to protect it. First, define your stance on PHI, what information is included, how you will protect it, and the acceptable use of this data. Then you can use your guidelines to ensure your organization protects patients to the best of your ability and limit your exposure to penalty.
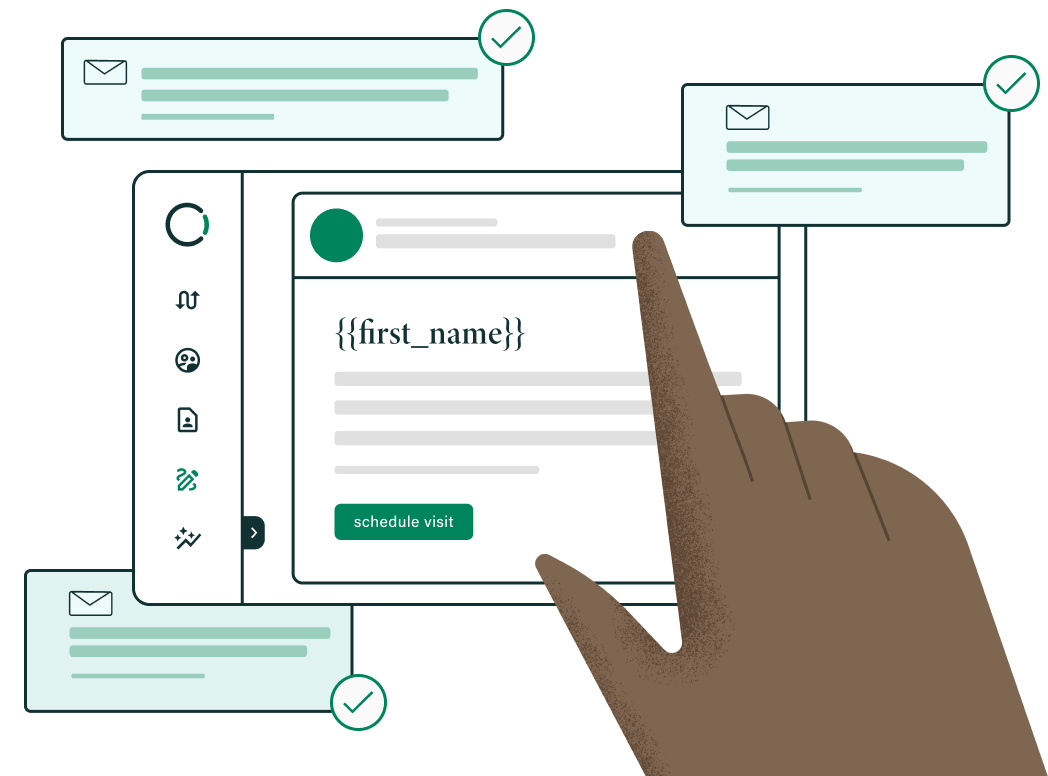
HIPAA-Compliant Email
According to the HIPAA Journal, HIPAA compliance for email require covered entities and business associates to implement access controls, audit controls, integrity controls, ID authentication, and transmission security mechanisms to:
- Restrict access to PHI
- Monitor how PHI is communicated
- Ensure the integrity of PHI at rest
- Ensure 100% message accountability, and
- Protect PHI from unauthorized access during transit
Encrypting the emails end-to-end allows you send to preserve the confidentiality of your patients’ PHI is vital to ensure they are unreadable by anyone or any technology who may intercept them. To ensure proper compliance while using email, you must use a solution that not only encrypts all your PHI at rest but takes all available precautions to protect it while in transit. In the world of email, that means it must be encrypted end-to-end because encryption is a widely available security measure.
HIPAA-Compliant SMS
Most SMS messages are not HIPAA eligible when PHI is inside the message because they cannot be encrypted, and copies of messages remain on service providers' servers. The only resolution to these issues is to exclude any PHI from messages sent in SMS format. We recommend using PHI in SMS to target and build audiences and limit inserting PHI into the content of the message.
What Happens if You Aren’t Compliant
Ignoring proper PHI protections puts your organization and your patients at extreme risk. Paying close attention to your and your vendor’s HIPAA stance will allow you to use digital marketing strategies to reach patients in their preferred communication channels.
HIPAA violations come with stiff penalties. According to the U.S. Department of Health and Human Services, civil and criminal penalties can be enforced. Breaches risk your organization’s reputation and come with significant fines, ranging from $10,000 to $50,000.
Many organizations claim to do this but don’t get fooled by companies claiming HIPAA eligibility and signing business associate’s agreements (BAAs). No single third party verifies HIPAA compliance. Companies self-identify HIPAA eligibility, meaning you must take their word for it. Their ability to sign a Business Associate’s Agreement with you does not necessarily mean they allow you to store, manage, or use PHI in their platforms.
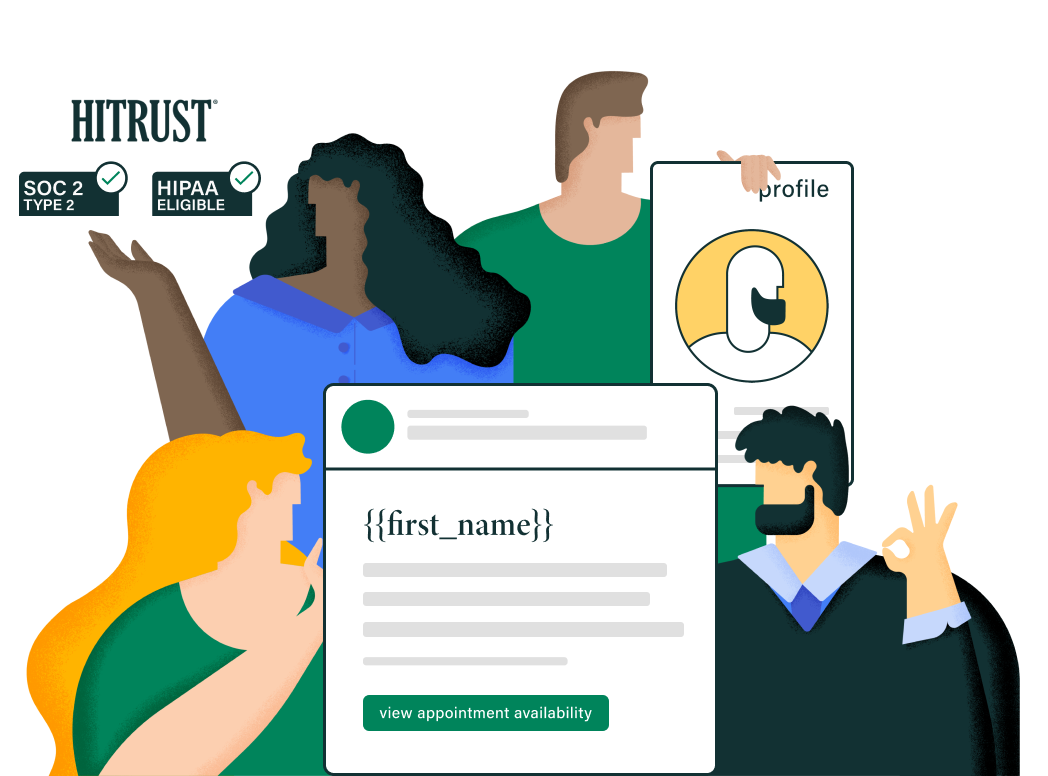
The HIPAA- and HITRUST-Compliant Digital Marketing Solution
HIPAA regulations for email and SMS are incredibly complex. Selecting a platform that prioritizes its commitment to security and compliance enables you to maintain your reputation, protect customers, and stay ahead of the competition.
Cured’s platform follows HIPAA guidelines and compliantly manages PHI. Our HITRUST certification and SOC 2 Type 2 attestation further support protecting your organization and patient data. Our compliance and security policies and processes are reviewed continuously, both internally and externally, to ensure continued effectiveness.
HITRUST
HITRUST is a third-party organization that delivers data protection standards and certification programs to help organizations safeguard sensitive information, manage information risk, and reach compliance goals. HITRUST is a healthcare-specific certification that verifies a company uses the strictest requirements when handling high-risk data. HITRUST certification allows Cured to confidently store PHI and enable our customers to use it appropriately for their needs.
Security and privacy are more than just table stakes – they are a true differentiator. Cured was designed with rigorous compliance in mind, so you can build your digital marketing program knowing you have the tools you need to maintain customer trust and avoid privacy breaches.
Learn more about our stance on security and compliance here.



